|
The following CTF can be found at: Contextis WEP Trace I did not create this CTF. You have sniffed out a wireless network stream. Can you determine the encryption key used and identify any sensitive data?
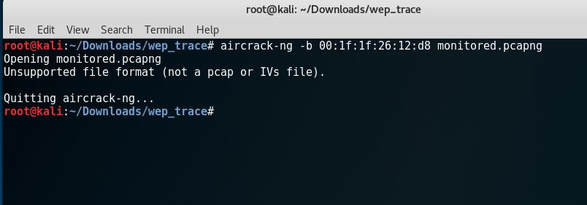
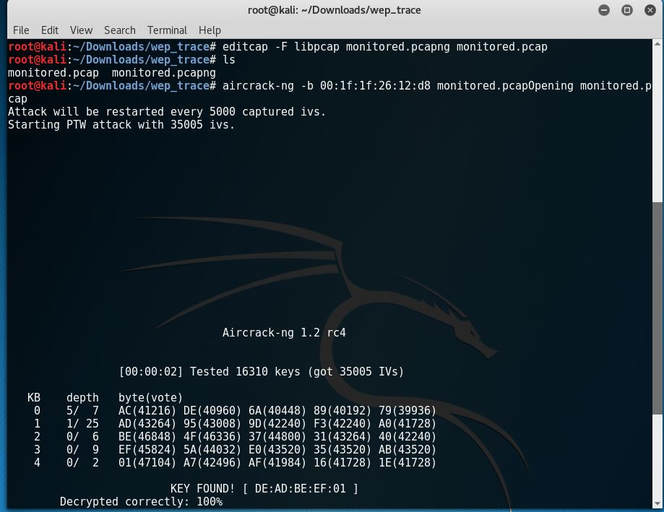
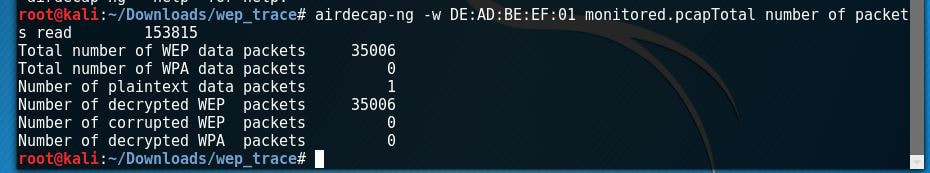
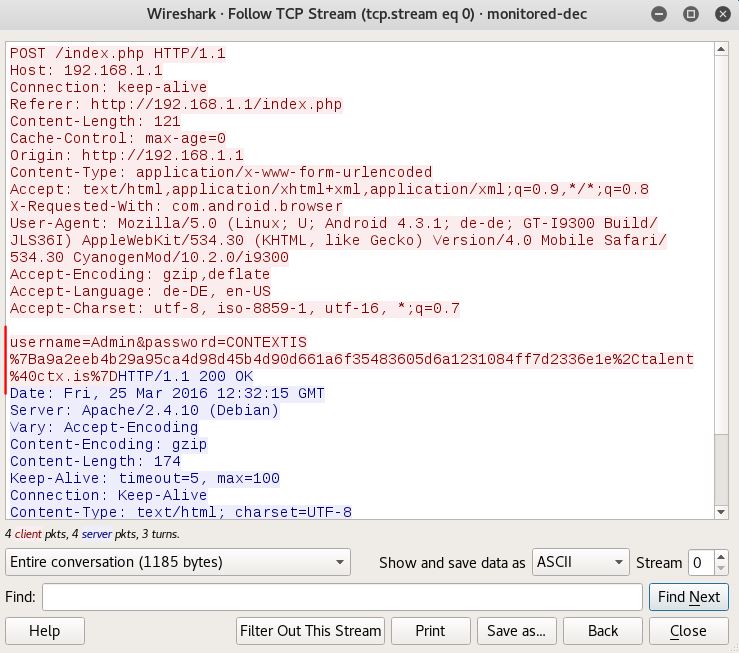
The first thing I notice is that it is a *.pcapng file extension, which I have never worked with. So I begin to do a bit of research and discover that it stands for pcap Next Generation. Now normally I wouldn't care too much, but after I tried to attack the file I received this error: After doing some more research I discover a tool called editcap that whenever using the libpcap library allows you to convert *.pcapng file types back to *.pcap. After I converted the file, aircrack-ng was happy to begin the PTW attack and below is the deciphered key: [DE:AD:BE:EF:01] Next, I began to decrypt the WEP packets with airdecap-ng. I then opened up the file, set the expression to follow the TCP stream and low and behold the username and password were displayed!
0 Comments
Leave a Reply. |
|||||||||
Hope you have enjoyed your stay! Come back again!
This site is under constant (slow) construction. Thank you for your patience.
Created by Moses J. Arocha ©
This site is under constant (slow) construction. Thank you for your patience.
Created by Moses J. Arocha ©